Implementing a comprehensive WordPress Security Checklist is essential for fortifying your site, considering WordPress’s status as the leading content management system with a staggering 810 million websites. Despite its robust security, the platform’s popularity makes it a prime target for cyber threats. Regular updates are crucial, but improper website management practices can compromise WordPress security.
No-Code WordPress Security Checklist
Site owners can seamlessly implement essential WordPress security practices even sans technical know-how. Safeguard your site, data, and visitors with these strategies.
Opt for a Secure WordPress Host
Managing your WordPress site can be daunting, especially without technical prowess. Secure WordPress hosting offers a worry-free experience, placing the responsibility on others for site security. Key features include:
- A secure hosting infrastructure
- Timely WordPress, plugin, and theme updates
- SSL certificates for enhanced encryption
- 24/7 monitoring of both your site and its hosting infrastructure
- Comprehensive website backups
Regular Backups
While backups primarily serve disaster recovery, they play a pivotal role in softening the blow of a breach. Recent backups act as a shield against ransomware or malware, averting data loss.
Determining the backup frequency hinges on practicality. For a bustling website, real-time backups pose challenges. Assess the acceptable data loss—be it a day’s transactions or a week’s posts, known as the Recovery Point Objective (RPO).
Craft a backup schedule aligned with your RPO. Implement the widely-used 3-2-1 Backup Strategy:
- Maintain 3 copies of your WordPress data
- Store 2 copies on diverse storage media (e.g., USB and cloud storage)
- Keep 1 copy offsite
This strategy safeguards against media failure and provides offsite protection, crucial in unforeseen events like data center fires or ransomware attacks.
Employ a WordPress Security Plugin
To fortify your site against online threats, a WordPress security plugin stands as the frontline guardian. These plugins excel in handling intricate security tasks, sparing you the need for technical know-how in areas like .htaccess file edits, web server configurations, firewall setup, and malware detection and removal.
Top contenders in the realm of security plugins include:
- Wordfence (boasting over 4 million active installs)
- All-In-One Security (AIOS) with an impressive 1 million+ active installs
- Sucuri Security, trusted by over 800,000 users
These plugins ensure a robust shield for your WordPress site, making security intricacies more manageable for every site owner.
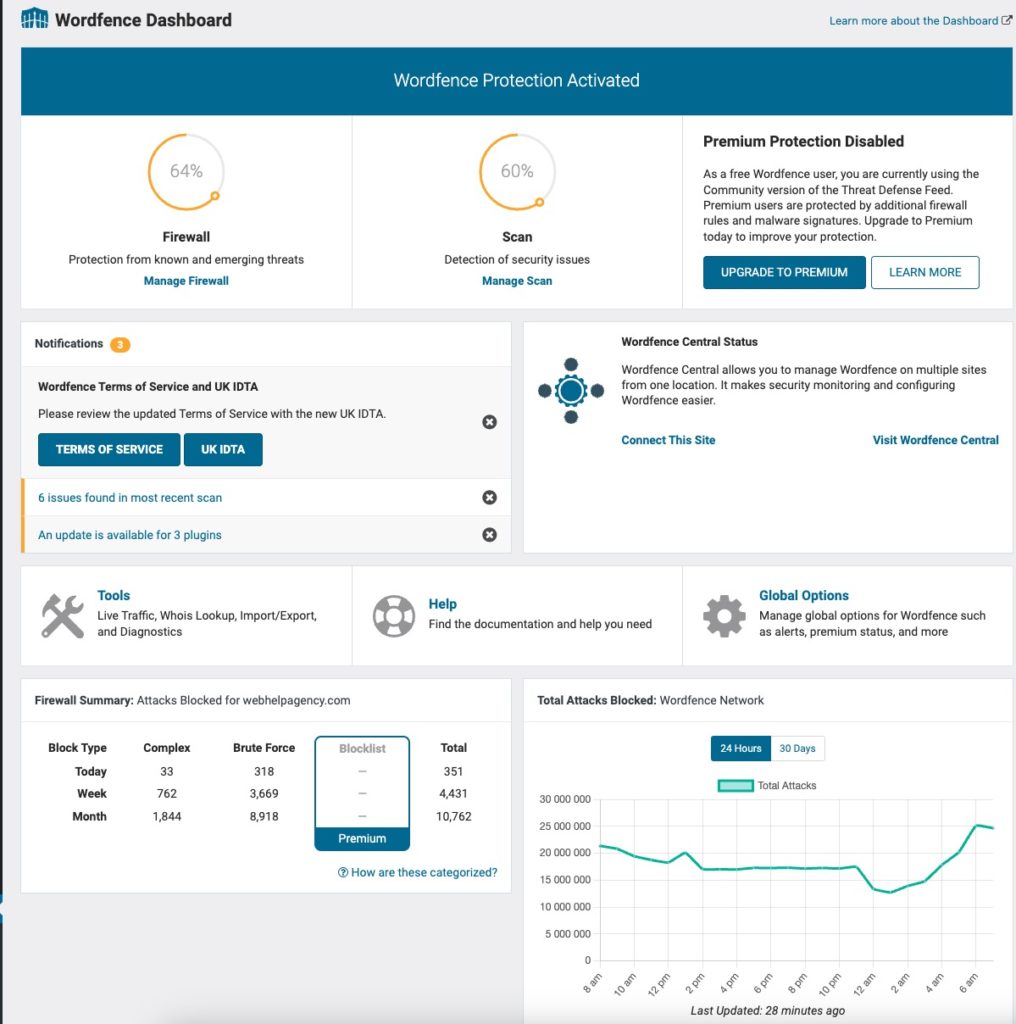
Upon installation, activating key features amplifies your site’s security:
- Limit Login Attempts:
- Thwart brute force attacks by restricting login trials, and enhancing WordPress security.
- Specify a lockout duration for any trespasser attempting unauthorized logins.
- Disable File Editing:
- Eliminate a security loophole by deactivating the theme file editor.
- Mitigate the risk of an intruder escalating their WordPress role or gaining server access.
- Disable PHP File Execution:
- Safeguard the /uploads directory from malicious code execution.
- Restrict this directory to storing static content, deterring compromised plugins or attacker-uploaded files.
- Enable Two-Factor Authentication (2FA):
- Elevate authentication security by implementing 2FA.
- Require a code from a mobile app, such as Google Authenticator, alongside the username and password.
- Prevent Directory Listings:
- Conceal WordPress directory contents to deter attackers.
- Safeguard sensitive information, including installed themes and plugins, by disabling directory listings.
- Hide WordPress Version:
- Adopt a “security through obscurity” approach by concealing your WordPress version.
- This minimizes the risk of attackers exploiting vulnerabilities associated with specific versions.
Wordfence, based on personal experience, emerges as a steadfast security ally. However, installing a security plugin is just one facet; embracing robust security practices completes the equation for comprehensive WordPress security.
Secure Your Website with an SSL Certificate
In the contemporary web landscape, SSL certificates are integral components of hosting packages. These certificates, part of the Secure Sockets Layer, encrypt data exchanged between browsers and web servers, ensuring tamper-free transmissions.
A quick check for a padlock icon in the address bar and the preceding “https://” in your site’s URL confirms the presence of an SSL certificate.
If your site lacks SSL protection, consult your hosting provider. SSL certificates, ranging from free to premium, should align with your data transmission needs. Brochure sites and blogs often suffice with LetsEncrypt’s free SSL certificates. However, handling sensitive data like credit card details may necessitate advanced certificates like Organization Validation (OV) or Extended Validation (EV) for PCI DSS compliance.
Keep Everything Updated
Maintaining the latest WordPress core, plugins, and themes is paramount in thwarting potential security vulnerabilities. Regularly perusing Wordfence’s Weekly Vulnerability Reports consolidates plugin vulnerabilities for quick and easy consumption. The emphasis is clear: keeping your WordPress components up to date is fundamental.
Fortuitously, WordPress facilitates automatic updates for the core, plugins, and themes. Although sporadic plugin updates may pose a risk of breaking your site, mitigating this concern involves testing updates on a staging site or opting for a WordPress maintenance service.
To enable auto-updates for plugins, access Plugins > Installed Plugins in your WordPress dashboard. Click on Auto-updates Disabled, select all plugins, choose Enable Auto-updates, and click Apply.
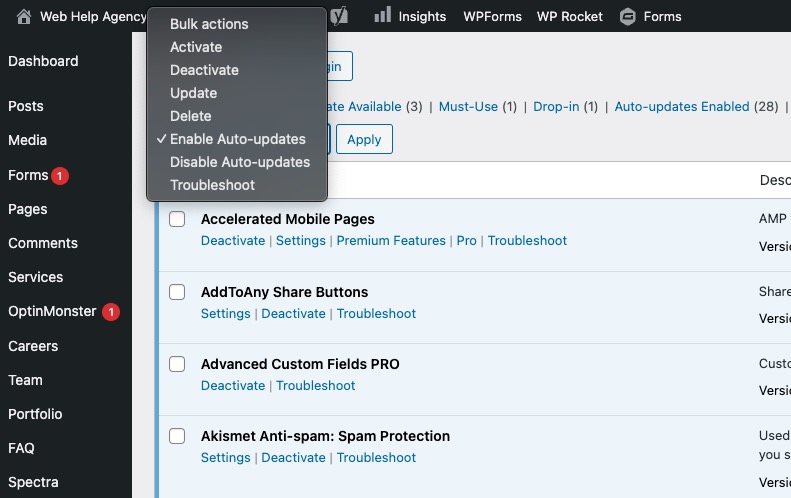
Notably, this feature may not apply to all plugins, particularly premium ones that may necessitate manual updates.
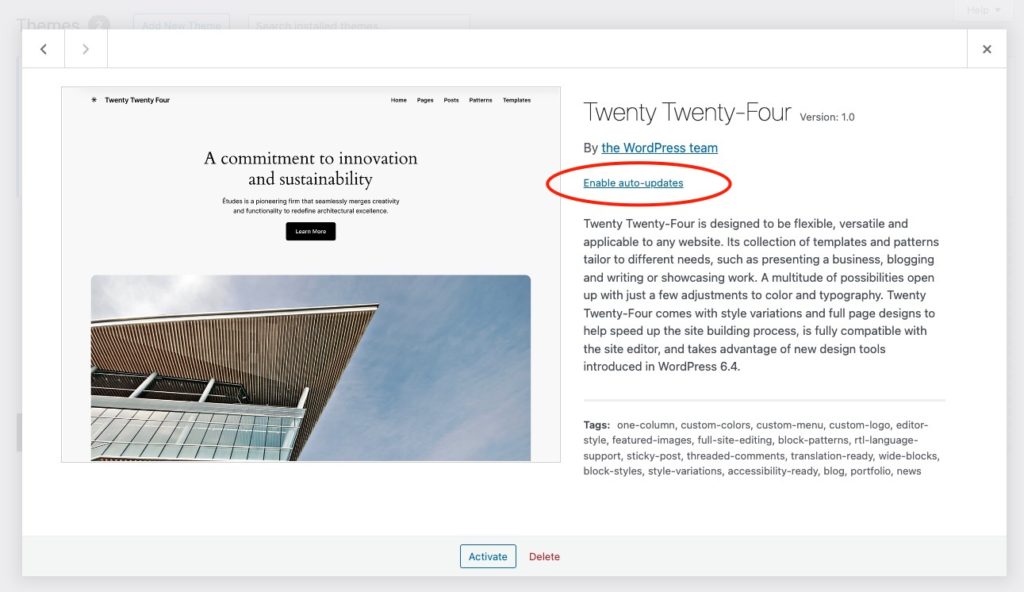
For theme auto-updates, navigate to Appearance > Themes, click your theme’s thumbnail, and select Enable auto-updates below the theme author.
Handling WordPress core updates involves distinguishing between major and minor versions. Major updates introduce new features, while minor updates focus on bug fixes, security, and maintenance. Minor automatic updates are enabled by default, and you can activate auto-updates for both major and minor versions in Dashboard > Updates by clicking Enable automatic updates for all new versions of WordPress.
Optimize WordPress Security with Plugin and Theme Best Practices
Mitigating potential vulnerabilities tied to plugins and themes requires strict adherence to best practices. Take these crucial steps for page-speed optimization:
- Delete Inactive Plugins:
- Inactive plugins are not harmless; their files may harbor vulnerabilities even when deactivated.
- Neglecting updates for inactive plugins can leave potential exploits unpatched.
- Inactive plugins, if accidentally activated, expand the site’s attack surface.
- Keep Your Footprint Small:
- Limit the number of plugins and themes to reduce your website’s attack surface.
- Opt for plugins like Crocoblock’s JetEngine or Advanced Custom Fields for custom functionality.
- Consider a barebones theme like Elementor’s Hello theme paired with a page builder plugin to minimize plugin dependency.
- Maintain a Trusted Vendor List:
- The open nature of WordPress allows anyone to create plugins or themes, leading to varying coding standards.
- Enhance security by using plugins and themes only from trusted authors with best practices.
- Regularly check for vulnerabilities using OpenCVE and ensure prompt patch releases from authors.
Remember, downloading ‘nulled’ plugins can introduce malicious code, compromising your website’s security. Always obtain plugins from the official developer or vendor’s website.
Fortify Your WordPress Credentials
Enhancing WordPress security involves treating your username and password as distinct layers, amplifying protection against brute force attacks. These attacks, powered by automated scripts, systematically test numerous username and password combinations to breach your account swiftly.
To bolster your defense:
- Avoid Common Usernames:
- Steer clear of generic usernames like admin, root, or test.
- Ditch easily guessable options to thwart brute force attempts.
- Elevate your site’s security by choosing unique and less predictable usernames.
- Craft Robust Passwords:
- Ensure passwords are a minimum of 12 characters long.
- Embrace complexity with a mix of uppercase letters, lowercase letters, numbers, and special characters.
- Choose unique words devoid of dictionary entries, brand names, or easily guessable terms.
- Check Password Exposure:
- Verify password integrity against data breaches using tools like Have I Been Pwned.
- Leverage Scattered Secrets (requires free signup) to monitor email and password exposure in data breaches.
By adopting these measures, you fortify your WordPress fortress against unauthorized access, reducing vulnerability to common attack vectors.
Refine WordPress Access Control: User Roles
Beyond the realm of email addresses and passwords lies the domain of WordPress authorization—how much access you grant your users. The critical consideration here is minimizing potential breaches caused by lost or stolen credentials.
Embrace the principle of least privilege when adding users, ensuring each user is granted only the essential privileges required for their role. WordPress offers built-in roles, each tailored to specific functions:
- Super Admin: Governs all features across a WordPress multisite with subdomains setup.
- Administrator: Commands all features within a single site.
- Editor: Manages posts, including those by other users.
- Author: Manages solely their own posts.
- Contributor: Writes posts but lacks publishing authority.
- Subscriber: Limited to managing their own profile.
For more nuanced control or custom roles, User Role Editor, a plugin, proves valuable, though it demands cautious use. Dive into the WordPress Roles and Capabilities page for a comprehensive understanding of individual role capabilities. Adopting a meticulous approach to user roles fortifies your WordPress security architecture.
Elevate Your WordPress Security: Advanced Measures
For these advanced WordPress security tips, access to server files is essential. If command-line access is unavailable, utilize an FTP client like FileZilla for file download and upload post-changes.
As a fundamental precaution, always create a comprehensive backup of your WordPress website, including the database.
Preventing WordPress Directory Listings
To grasp the importance, perform a quick Google search for “index of wp-content.” The results, such as “index of /wp-content/uploads,” can expose vulnerabilities:
- Access to Sensitive Files:
- Directory listings might reveal unprotected sensitive files, posing a security risk.
- Backup copies with stored database credentials in wp-config.php could be accessible.
- Identification of Installed Themes and Plugins:
- Easily discern which themes and plugins are installed on your website.
- Custom code with sensitive information might be exposed.
- Understanding Directory Structure:
- Provides insights into your site’s directory structure, aiding potential attackers.
To safeguard against these risks:
- Modify .htaccess File:
- Open the .htaccess file in your site’s root directory and add:
Options -Indexes- Alternatively, create an empty index.html file in each directory.
Note: Some WordPress security plugins automatically prevent directory listings, eliminating the need for manual intervention.
Manually-Code WordPress Security Checklist
Changing Table Prefix Manually
The WordPress database houses crucial site information, making it a prime target for attackers, particularly during SQL injection attacks exploiting plugin vulnerabilities. A common target is the standardized wp_users table, where user credentials reside.
While changing the table prefix is simplest during installation, existing WordPress sites require direct database modifications through MySQL prompt or phpMyAdmin. Follow these steps:
- Backup Everything:
- Safeguard your entire WordPress database with a comprehensive backup. Test changes first on a staging or development site.
- Update wp-config.php:
- Locate the line in wp-config.php setting the table prefix. Change it to a random string, like ‘wD711_’:
$table_prefix = ‘wD711_’;- Rename Database Tables:
- Execute queries via MySQL prompt or phpMyAdmin to rename core tables, e.g.:
RENAME table wp_commentmeta TO wD711_commentmeta;
RENAME table wp_comments TO wD711_comments;
... (repeat for other tables)- Update Options & Usermeta:
- Further, modify options and usermeta using SQL queries:
UPDATE wD711_options SET option_name = REPLACE(option_name, ‘wp_’, ‘wD711_’) WHERE option_name LIKE ‘wp\_%’;
UPDATE wD711_usermeta SET meta_key = REPLACE(meta_key, ‘wp_’, ‘wD711_’) WHERE meta_key LIKE ‘wp\_%’;- Test Extensively:
- Testing is crucial, especially for plugins hardcoded with ‘wp_’ prefixes that may cause functionality errors.
By meticulously following these steps, you bolster your WordPress security, rendering it more resilient against potential attacks.
Disable File Editing and Manage Plugins and Themes
To bolster security, manually disable file editing in the WordPress Dashboard by adding the following line to wp-config.php:
define('DISALLOW_FILE_EDIT', true);This action removes the file editor from the Appearance menu.
For additional security, eliminate plugin and theme management from the WordPress Dashboard. In case of unauthorized access, add the following line to wp-config.php:
define('DISALLOW_FILE_MODS', true);Note: Ensure file editing is disabled for this to take full effect. Implementing these measures fortifies your WordPress site against potential vulnerabilities.
Conceal WordPress Version Manually: A Step-by-Step Guide
While I’ve touched on hiding the WordPress version, executing this manually involves edits in various areas. Ensure a safe process by testing on a staging site and creating backups before commencing:
- Remove Version from Header Tags:
- Safeguard your website’s header by adding this line to your theme’s functions.php file:
remove_action('wp_head', 'wp_generator');Erase Version from RSS Feeds:
- Ensure version anonymity in RSS feeds by incorporating the following code into your theme’s functions.php file:
function remove_wp_version_rss() {
return '';
}
add_filter('the_generator', 'remove_wp_version_rss');Implementing these steps assures the manual hiding of your WordPress version, reinforcing security without compromising functionality.
Conceal WordPress Version Across Various Elements
To bolster security, follow these steps to remove the WordPress version from script and style tags in your theme’s functions.php file:
function remove_script_version($src) {
return $src ? esc_url(remove_query_arg('ver', $src)) : false;
}
add_filter('script_loader_src', 'remove_script_version', 10, 1);
add_filter('style_loader_src', 'remove_script_version', 10, 1);Additionally, eliminate the WordPress version from the admin panel footer by adding this code to your theme’s functions.php file:
function remove_wp_version_footer_admin() {
remove_filter('update_footer', 'core_update_footer');
}
add_action('admin_menu', 'remove_wp_version_footer_admin');For older WordPress versions, blocking access to readme.html is crucial. If updates aren’t feasible, secure your site by adding the following to .htaccess in the site’s root directory:
<Files “readme.html”>
Order allow,deny
Deny from all
</Files>Implementing these measures ensures a more secure WordPress site without compromising functionality.
Wrap it Up
After implementing these WordPress security measures, it’s vital to establish ongoing practices. While some, like selecting a secure host and enabling auto-updates, are one-time tasks, security is an ongoing commitment. Incorporate regular backups into your routine, stay vigilant about users, plugins, and themes, and subscribe to security email lists for prompt vulnerability alerts. Though time-intensive, these efforts fortify your site against potential threats and ensure a swift recovery in case of a breach.
Alternatively, leverage the convenience of Web Help Agency’s WordPress maintenance service, where security and backups are seamlessly managed. This allows you to allocate your time efficiently, entrusting the responsibility of safeguarding your site and visitors to a reliable WordPress host while you concentrate on essential tasks.
